VMware Cloud Director 10.5 GA Workaround for CVE-2023-34060
Article ID: 320464
Updated On:
Products
VMware Cloud Director
Issue/Introduction
VMware Cloud Director 10.5.1 addresses an authentication bypass vulnerability.
The Common Vulnerabilities and Exposures project (https://cve.mitre.org) has assigned the identifier CVE-2023-34060 to this issue.
VMware released VMware Security Advisory VMSA-2023-0026 to help customers understand the issue and which upgrade path will fix it.
This article lists the recommended solution, upgrading to a patched release, but also provides a workaround for customers who can't upgrade.
Environment
VMware Cloud Director 10.x
Resolution
This is a known issue in VMware Cloud Director 10.5.0.
This issue is specific to appliance deployments and those that have been upgraded.
Customers are strongly recommended to upgrade to one of these applicable versions immediately.
If upgrading to a recommended version is not an option, you may apply this Workaround below.
Workaround:
If you are running an Appliance based server group which has been upgraded from a previous version of Cloud Director, it is recommended you run the script detailed below.
Note:
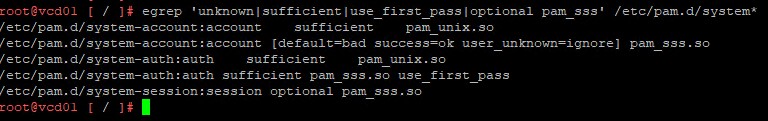
Whilst the script will perform verification prior to making any changes, if you wish to manually verify if your Cell is exposed to the vulnerability you can run the following command:
If you receive any output from the above command, you will need to execute the script. (example output below)
Perform the following steps: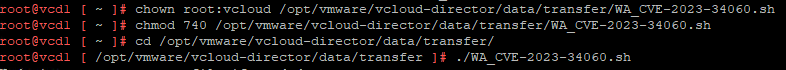
Script Output for an affected Appliance Cell:
Script Output for an unaffected/patched Appliance Cell:
This issue is specific to appliance deployments and those that have been upgraded.
- This issue does not apply to Linux deployments.
- This issue does not apply to fresh installs of VMware Cloud Director 10.5.0.
- This issue does not apply to Cloud Director Service (CDS) instances of Cloud Director.
Customers are strongly recommended to upgrade to one of these applicable versions immediately.
| Affected VMware Cloud Director Version | Fixed Version | Release Date |
| 10.5.0 | 10.5.1 | November 30th 2023 |
If upgrading to a recommended version is not an option, you may apply this Workaround below.
Workaround:
If you are running an Appliance based server group which has been upgraded from a previous version of Cloud Director, it is recommended you run the script detailed below.
Note:
- Following the application of the workaround, any subsequent upgrade or patching of Cells to a build which is not a Fixed Version will revert the workaround.
- Similarly, deploying Cells from a non-patched build will also result in the workaround not being applied. The script will need to be run on these newly deployed Cells.
- There is no functionality impact as a result of implementing this workaround
Whilst the script will perform verification prior to making any changes, if you wish to manually verify if your Cell is exposed to the vulnerability you can run the following command:
egrep 'unknown|sufficient|use_first_pass|optional pam_sss' /etc/pam.d/system*
If you receive any output from the above command, you will need to execute the script. (example output below)
Perform the following steps:
- SSH to Primary Cell within the Server Group.
- Download the attached WA_CVE-2023-34060.sh script to the /opt/vmware/vcloud-director/data/transfer/ directory.
- Modify the permissions of the file to allow execution.
- chown root:vcloud /opt/vmware/vcloud-director/data/transfer/WA_CVE-2023-34060.sh
- chmod 740 /opt/vmware/vcloud-director/data/transfer/WA_CVE-2023-34060.sh
- Navigate to the Transfer directory of the Cell.
- cd /opt/vmware/vcloud-director/data/transfer/
- Execute the script.
- ./WA_CVE-2023-34060.sh
- Repeat Step 4 and Step 5 above on all remaining Cells within the Server Group.
Script Output for an affected Appliance Cell:
Updating system-account file if needed
account [default=bad success=ok user_unknown=ignore] pam_sss.so
Removing account line from system-account file
Successfully removed account pam_sss.so line from system-account file
account sufficient pam_unix.so
Removing sufficient qualification from pam_unix.so entry in system-account file
Successfully removed sufficient qualification from pam_unix.so entry in system-account file
Updating system-auth file if needed
auth sufficient pam_sss.so use_first_pass
Removing account line from system-auth file
Successfully removed use_first_pass line from system-auth file
auth sufficient pam_unix.so
Removing sufficient qualification from pam_unix.so entry in system-auth file
Successfully removed sufficient qualification from pam_unix.so entry in system-auth file
Updating system-session file if needed
session optional pam_sss.so
Removing optional line from system-session file
Successfully removed optional line from system-session file
Script Output for an unaffected/patched Appliance Cell:
Updating system-account file if needed
No changes were needed to system-account file to remove the account pam_sss.so reference.
No changes were needed to system-account file to remove sufficient qualification from pam_unix.so entry.
Updating system-auth file if needed
No changes were needed to system-auth file to remove use_first_pass reference.
No changes were needed to system-auth file to remove sufficient qualification from pam_unix.so entry
Updating system-session file if needed
Updates to system-session file were not needed.Additional Information
Below table shows an affected and unaffected/patched version of the files in question.
Impact/Risks:
This workaround is applicable to affected versions of VMware Cloud Director 10.5.0.
Do not apply this workaround to other VMware products.
| File | File Contents |
| Affected /etc/pam.d/system-account | # Begin /etc/pam.d/system-account account required pam_tally2.so file=/var/log/tallylog account sufficient pam_unix.so account [default=bad success=ok user_unknown=ignore] pam_sss.so # End /etc/pam.d/system-account |
| Unaffected /etc/pam.d/system-account | # Begin /etc/pam.d/system-account account required pam_tally2.so file=/var/log/tallylog account required pam_unix.so # End /etc/pam.d/system-account |
| Affected /etc/pam.d/system-auth | # Begin /etc/pam.d/system-auth auth required pam_env.so auth required pam_tally2.so onerr=fail deny=3 unlock_time=900 root_unlock_time=900 file=/var/log/tallylog auth sufficient pam_unix.so auth sufficient pam_sss.so use_first_pass auth optional pam_faildelay.so delay=4000000 # End /etc/pam.d/system-auth |
| Unaffected /etc/pam.d/system-auth | # Begin /etc/pam.d/system-auth auth required pam_env.so auth required pam_tally2.so onerr=fail deny=3 unlock_time=900 root_unlock_time=900 file=/var/log/tallylog auth required pam_unix.so auth optional pam_faildelay.so delay=4000000 # End /etc/pam.d/system-auth |
| Affected /etc/pam.d/system-session | # Begin /etc/pam.d/system-session session required pam_unix.so session optional pam_sss.so session required pam_limits.so session optional pam_motd.so session optional pam_lastlog.so silent session optional pam_systemd.so # End /etc/pam.d/system-session |
| Unaffected /etc/pam.d/system-session | # Begin /etc/pam.d/system-session session required pam_unix.so session required pam_limits.so session optional pam_motd.so session optional pam_lastlog.so silent session optional pam_systemd.so # End /etc/pam.d/system-session |
Impact/Risks:
This workaround is applicable to affected versions of VMware Cloud Director 10.5.0.
Do not apply this workaround to other VMware products.
- There is no functionality impact as a result of implementing this workaround.
- Downtime will not be required as neither a service restart nor reboot are required.
Attachments
Feedback
Yes
No
