LDAPS may stop working after upgrading NSX to version 4.1.0
Article ID: 322433
Updated On:
Products
VMware NSX Networking
Issue/Introduction
Symptoms:
- LDAPS (default port 636) or LDAP with StartTLS is not working after upgrading NSX to version 4.1.0.
- Following error is generated when re-adding LDAPS in the VMware NSX UI, and can be seen the log files /var/log/proton/policy-ui.log, /var/log/syslog and /var/log/proton/nsxapi.log:
"Error: Unable to obtain server certificate. Communication error. Verify that the IP address/hostname, port, and other parameters are correct. (Error code: 53000)."
- If Identity firewall (IDFW) is configured, it may have stopped working and the LDAP server configured for IDFW status is shown as DOWN.
- LDAP (port 389) will continue to work.
- From NSX manager connection to LDAP server on port 636 is successful:
nc -vz <ldaps-server> 636
- Packet capture on NSX manager, while running connection status check from NSX manager UI, shows connection reset from LDAP server.
Environment
VMware NSX 4.1.0
Cause
This issue occurs due to the older, insecure TLS cipher suites being disabled in NSX 4.1, in the proton service. If the LDAP server is an older version that does not support the more secure cipher suites that NSX uses, connections may fail. LDAP servers must also support at least TLS version 1.2, or connections will fail. TLS versions 1.1 and earlier are now considered insecure and NSX does not support them by default.
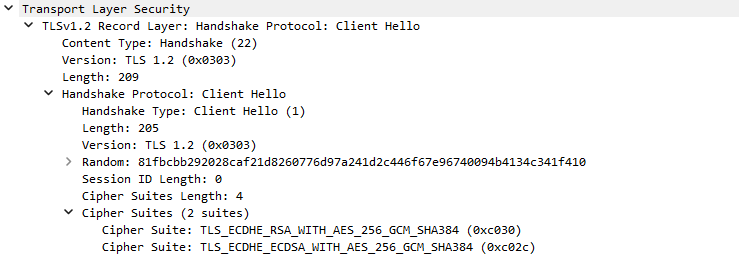
Cipher suites now used by VMware NSX 4.1 and onwards:
Cipher suites used by previous versions of VMware NSX:
- IDFW uses the proton service for connections and this issue can therefore lead to issues with IDFW.
- User login/logout events do not user proton, but a separate service and are not affected by the cipher suite change.
- LDAP server connection status uses the proton service and is therefore impacted by the cipher suite change.
Cipher suites now used by VMware NSX 4.1 and onwards:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
Cipher suites used by previous versions of VMware NSX:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_GCM_SHA256
Resolution
Ensure the LDAPS or LDAP with StartTLS server is using a supported, secure cipher suite as listed above.
Workaround:
If you believe you have encountered this issue and are unable to upgrade the LDAPS or LDAP with StartTLS server cipher suite at this time, please open a support request with VMware NSX-T GSS and refer to this KB article.
For more information, see How to Submit a Support Request.
Workaround:
If you believe you have encountered this issue and are unable to upgrade the LDAPS or LDAP with StartTLS server cipher suite at this time, please open a support request with VMware NSX-T GSS and refer to this KB article.
For more information, see How to Submit a Support Request.
Feedback
Yes
No
