Replace expired internal certificate in vRealize Log Insight 8.10 and lower
Article ID: 342206
Updated On:
Products
VMware Aria Suite
Issue/Introduction
This article provides steps to install a new internode communication certificate in vRealize Log Insight 8.10.x or below.
Symptoms:
Symptoms:
- The internal internode communication certificate in vRealize Log Insight 8.10.x or below is expired.
Environment
VMware vRealize Log Insight 8.6.x
VMware vRealize Log Insight 8.8.x
VMware vRealize Log Insight 8.10.x
VMware vRealize Log Insight 8.8.x
VMware vRealize Log Insight 8.10.x
Resolution
To resolve the issue, follow the steps below to install a new internode communication certificate.
Quick Links:
Note: This command will generate a self-signed certificate that is valid for 3650 days (10 years). You may alter the -days value as needed per your organization's security requirements.
Note: When prompted by openssl, provide the required values for your company. If you want to use the default certificate options, enter the following values:
Quick Links:
Prerequisites
- This workaround requires a .pem certificate file to be uploaded.
- If you have a custom certificate, using an SCP utility like WinSCP, upload the .pem file to the /tmp directory on all nodes in the vRealize Log Insight cluster.
Note: VMware Aria Operations 8.12 and later requires Client Auth usage. Ensure your custom certificate meets this requirement. You can run the echo | openssl s_client -connect localhost:443 2>/dev/null | openssl x509 -noout -purpose | grep 'SSL client :' command on a node with your custom certificate installed to confirm.
If the above command returns SSL client : Yes, then you can proceed to the Install Certificate section.
If the above command returns SSL client : No, then you must regenerate your custom certificate with Client Auth enabled.
If the above command returns SSL client : Yes, then you can proceed to the Install Certificate section.
If the above command returns SSL client : No, then you must regenerate your custom certificate with Client Auth enabled.
- If you want to use the default certificate, you will need to Generate a self-signed certificate for use.
Generate a self-signed certificate
- Log into the Primary node as root via SSH or Console.
- Run the following command to generate a self-signed certificate:
openssl req -newkey rsa:2048 -keyout domain.key -x509 -days 3650 -out domain.crt -nodes
Note: This command will generate a self-signed certificate that is valid for 3650 days (10 years). You may alter the -days value as needed per your organization's security requirements.
Note: When prompted by openssl, provide the required values for your company. If you want to use the default certificate options, enter the following values:
| Prompt | Value |
|---|---|
| Country | US |
| State Or Province | California |
| Locality | Palo Alto |
| Organization | VMware, Inc. |
| Organization Unit | vCenter Log Insight |
| Common Name | VMware vCenter Log Insight |
- Run the following command to concatenate the key and certificate into a .pem file
cat domain.key domain.crt > /tmp/cert.pem
- Using an SCP utility like WinSCP, copy the /tmp/cert.pem file from the Primary node to the /tmp directory on the other Worker nodes in the cluster.
Install Certificate
Note: The following steps must be completed on each node in the vRealize Log Insight cluster. This can be done sequentially or in parallel.- Download the fix_expired_cert_v2.tar file attached to this article form the Attachments section on the right.
- Using an SCP utility like WinSCP, copy the fix_expired_cert_v2.tar file to the /tmp directory on the Primary node.
- Log into the Primary node as root via SSH or Console.
- Run the following command to change to the /tmp directory:
cd /tmp
- Run the following command to extract the script from fix_expired_cert_v2.tar:
tar xf fix_expired_cert_v2.tar
- Run the following command to update the permissions of the script:
chmod 744 fix_expired_cert.sh
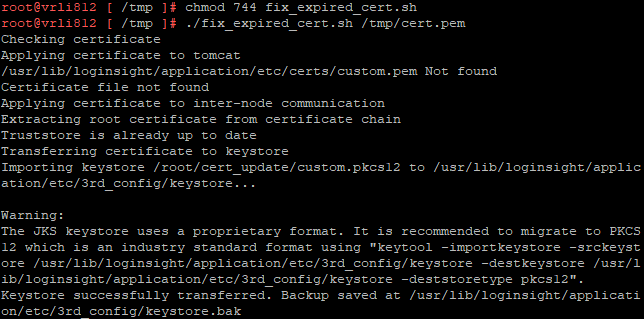
- Run the following command to run the fix_expired_cert.sh script:
./fix_expired_cert.sh pem_location
Note: Replace pem_location with the name of the certificate file from the Prerequisites that you plan to use.
Example: ./fix_expired_cert.sh /tmp/cert.pem
Note: Replace pem_location with the name of the certificate file from the Prerequisites that you plan to use.
Example: ./fix_expired_cert.sh /tmp/cert.pem
- Run the following command to verify that the script completed successfully:
./fix_expired_cert.sh --verify
Example: The output will be similar to:
Cluster certificate fingerprint is: <ID_1>
Inter-node certificate fingerprint is: <ID_1>
Root certificate fingerprint is: <ID_2>
Cluster and inter-node certificates are same
Found alias with matching root fingerprint
loginsight2:04:39:E4:63:1A:BA:FB:06:18:02:7F:9F:0F:1C:1F:B6:96:B7:42:34
Example: The output will be similar to:
Cluster certificate fingerprint is: <ID_1>
Inter-node certificate fingerprint is: <ID_1>
Root certificate fingerprint is: <ID_2>
Cluster and inter-node certificates are same
Found alias with matching root fingerprint
loginsight2:04:39:E4:63:1A:BA:FB:06:18:02:7F:9F:0F:1C:1F:B6:96:B7:42:34
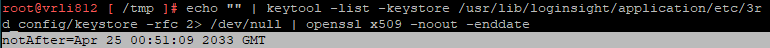
- Optional: Run the following command check the expiration date of the newly applied certificate to ensure the expiration date is in the future:
echo "" | keytool -list -keystore /usr/lib/loginsight/application/etc/3rd_config/keystore -rfc 2> /dev/null | openssl x509 -noout -enddate
Example:
- Run the following command to restart the loginsight service:
systemctl restart loginsight
- Repeat steps 1-10 on all nodes in the cluster, if they have not already been run.
Additional Information
Impact/Risks:
Important: This article is not applicable to VMware Aria Operations 8.12. Attempting to run these steps on VMware Aria Operations 8.12 may cause further harm to your cluster. To install a custom certificate in VMware Aria Operations for Logs 8.12 and later, see Install a custom certificate in VMware Aria Operations for Logs 8.12 and Later (93768).
If a new web certificate is applied to VMware Aria Operations for Logs (formerly known as vRealize Log Insight), the agents may disconnect. See Main SSL Functions for more information. It is recommended to Configure the vRealize Log Insight Agent SSL Parameters.
Important: This article is not applicable to VMware Aria Operations 8.12. Attempting to run these steps on VMware Aria Operations 8.12 may cause further harm to your cluster. To install a custom certificate in VMware Aria Operations for Logs 8.12 and later, see Install a custom certificate in VMware Aria Operations for Logs 8.12 and Later (93768).
If a new web certificate is applied to VMware Aria Operations for Logs (formerly known as vRealize Log Insight), the agents may disconnect. See Main SSL Functions for more information. It is recommended to Configure the vRealize Log Insight Agent SSL Parameters.
Attachments
Feedback
Yes
No
