Mitigation Instructions for CVE-2022-21123, CVE-2022-21125, and CVE-2022-21166 (VMSA-2022-0016)
Article ID: 318591
Updated On:
Products
VMware vSphere ESXi
Issue/Introduction
This article documents the VMware ESXi mitigations required to address the security vulnerabilities documented in VMSA-2022-0016
These vulnerabilities are only applicable to virtual environments with a PCI passthrough (VMDirectPath I/O pass-through) device configured. Ensuring that no virtual machine has such a configuration can be considered a viable workaround that will prevent any exploitation.
In addition, VMware have provided a release of both VMware ESXi 6.7 and VMware ESXi 7.0 which includes updates that allow for a new advanced setting named "VMkernel.Boot.forceHyperthreadingMitigation" to be configured. Once enabled, this will ensure that the ESXi host will be running the "ESXi Side-Channel-Aware Scheduler v2 (SCAv2)". This is a required step.
Enabling this option will impose the same performance impacts as the SCAv2 introduced in ESXi6.7U2.
These vulnerabilities are only applicable to virtual environments with a PCI passthrough (VMDirectPath I/O pass-through) device configured. Ensuring that no virtual machine has such a configuration can be considered a viable workaround that will prevent any exploitation.
In addition, VMware have provided a release of both VMware ESXi 6.7 and VMware ESXi 7.0 which includes updates that allow for a new advanced setting named "VMkernel.Boot.forceHyperthreadingMitigation" to be configured. Once enabled, this will ensure that the ESXi host will be running the "ESXi Side-Channel-Aware Scheduler v2 (SCAv2)". This is a required step.
Enabling this option will impose the same performance impacts as the SCAv2 introduced in ESXi6.7U2.
Environment
VMware vSphere ESXi 6.7
VMware vSphere 7.0.x
VMware vSphere 7.0.x
Resolution
Note: For VMware Cloud Foundation (VCF) Environments, Please follow KBs documented in the 'Impacted Product Suites that Deploy Response Matrix Components' table found in VMSA-2022-0016 first. Then, proceed with the steps mentioned below to add the advanced setting.
1) Patch the VMware ESXi host to the "Fixed Version" documented below
2) Enable the "VMkernel.Boot.forceHyperthreadingMitigation" advanced setting by changing the value to "True"
Configure the setting via the vSphere Client
1) Select the ESXi host in the inventory.
2) Click on "Configure, Advanced System Settings, Edit".
3) Search and find the "VMkernel.Boot.forceHyperthreadingMitigation" key and change the value from the default of false to true
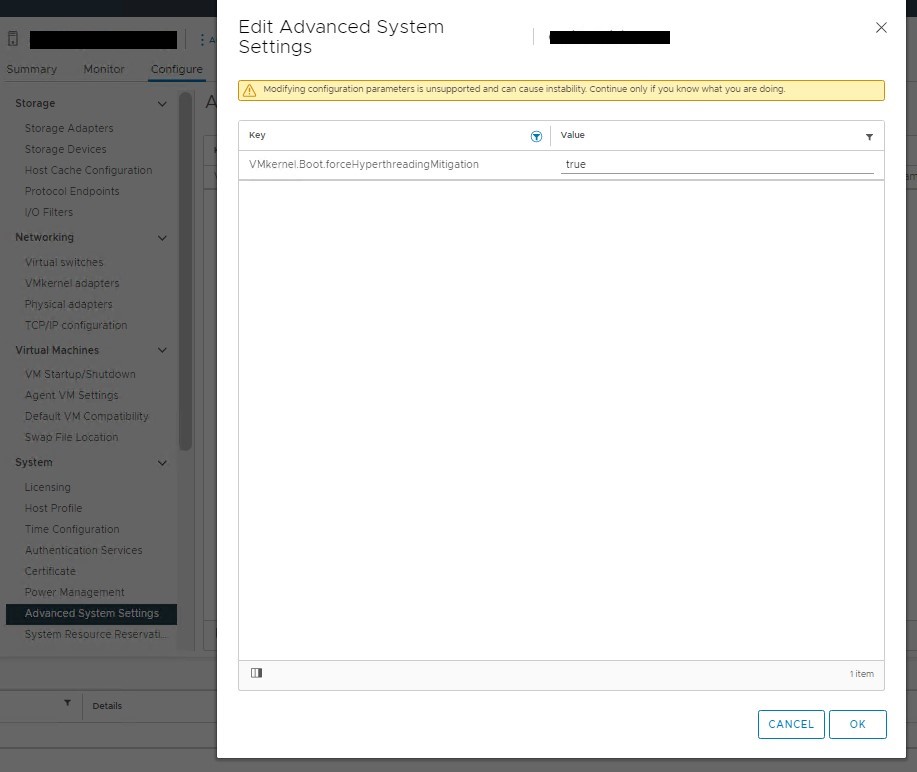
4) Click on Ok
5) Reboot the host to enable the setting
Configure the setting via Powercli
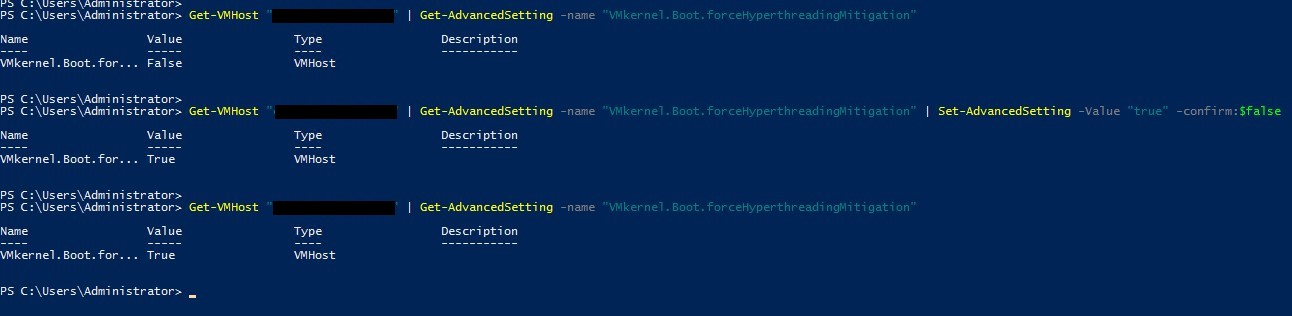
1) The "Set-AdvancedSetting" cmdlet can be used to configure the setting
Get-VMHost "%Name_ESXi_Host%" | Get-AdvancedSetting -name "VMkernel.Boot.forceHyperthreadingMitigation" | Set-AdvancedSetting -Value "true" -confirm:$false
1) Patch the VMware ESXi host to the "Fixed Version" documented below
| ESXi Version | Fixed Version |
| VMware ESXi 7.0 | ESXi 7.0 U3e (Release Notes) |
| VMware ESXi 6.7 | ESXi 6.7 P07 (Release Notes) |
| VMware ESXi 6.5 | Upgrade to 7.0 U3e (Preferred) or 6.7 P07 or Make sure VMs are not using PCI pass-through devices or Use PCI or PCIe passthrough to a virtual machine only if a trusted entity owns and administers the virtual machine. |
2) Enable the "VMkernel.Boot.forceHyperthreadingMitigation" advanced setting by changing the value to "True"
Configure the setting via the vSphere Client
1) Select the ESXi host in the inventory.
2) Click on "Configure, Advanced System Settings, Edit".
3) Search and find the "VMkernel.Boot.forceHyperthreadingMitigation" key and change the value from the default of false to true
4) Click on Ok
5) Reboot the host to enable the setting
Configure the setting via Powercli
1) The "Set-AdvancedSetting" cmdlet can be used to configure the setting
Get-VMHost "%Name_ESXi_Host%" | Get-AdvancedSetting -name "VMkernel.Boot.forceHyperthreadingMitigation" | Set-AdvancedSetting -Value "true" -confirm:$false
Additional Information
Change log:
- 02-Sep-2022 11:00am EST - Updated "ESXi 6.7 U3r" to "ESXi 6.7 P07" under Fixed Versions Table in Resolution section, as P07 is the patch version number updated in public documentations such as ESXi Build Numbers KB - https://kb.vmware.com/s/article/2143832
Feedback
Yes
No
