[VMC] Cloud vCenter Firewall Security Best Practices
Article ID: 334972
Updated On:
Products
VMware Cloud on AWS
VMware Cloud on Dell EMC
Issue/Introduction
To detail common best practices for securing a VMware Cloud vCenter.
Symptoms:
Customer received a Notification Gateway (NGW) Message stating they have a potentially insecure configuration live on their SDDC.
Symptoms:
Customer received a Notification Gateway (NGW) Message stating they have a potentially insecure configuration live on their SDDC.
Resolution
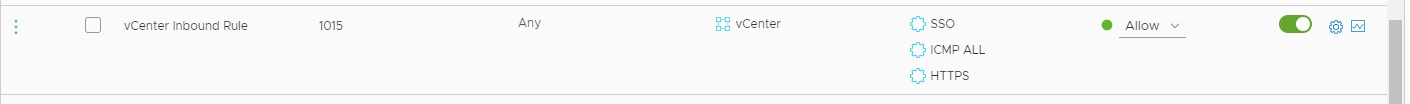
Customers will have received these NGW messages if they have configured an Any Source to vCenter Destination MGW firewall rule.
Having an Any source inbound firewall rule pointing to the Cloud vCenter goes against security best practices, exposing the Cloud vCenter to risk.
The correct course of action is to modify the offending firewall rule and update its source group to reference any Management Group which would require vCenter access.
Example Poor Rule (Any Source can access Cloud vCenter)
Example Updated Rule (Only a specific Desktop IP can access Cloud vCenter)
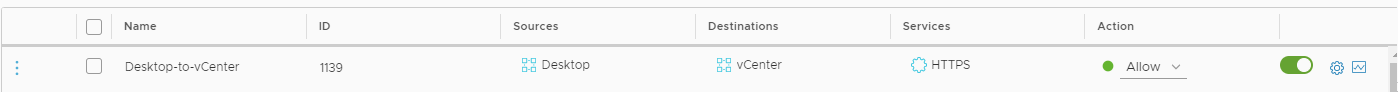
Having an Any source inbound firewall rule pointing to the Cloud vCenter goes against security best practices, exposing the Cloud vCenter to risk.
The correct course of action is to modify the offending firewall rule and update its source group to reference any Management Group which would require vCenter access.
Example Poor Rule (Any Source can access Cloud vCenter)
Example Updated Rule (Only a specific Desktop IP can access Cloud vCenter)
Additional Information
Impact/Risks:
Changing firewall Rules in a live production environment can always have unexpected consequences. Before publishing any firewall rule updates, double-check all rules changes to ensure VMC vCenter access will not be lost.
Changing firewall Rules in a live production environment can always have unexpected consequences. Before publishing any firewall rule updates, double-check all rules changes to ensure VMC vCenter access will not be lost.
Feedback
Yes
No
