Understanding the BPDU Filter feature in vSphere
Article ID: 305373
Updated On:
Products
VMware vCenter Server
VMware vSphere ESXi
Issue/Introduction
This article describes and provides examples on the BPDU filter feature in vSphere Distributed Switches.
Environment
VMware ESXi 3.5.x Embedded
VMware ESXi 4.0.x Installable
VMware vSphere ESXi 6.0
VMware vSphere ESXi 5.0
VMware vSphere ESXi 6.5
VMware ESXi 4.1.x Installable
VMware vCenter Server 5.5.x
VMware vSphere ESXi 8.0.x
VMware vSphere ESXi 5.1
VMware ESXi 4.0.x Embedded
VMware vSphere ESXi 5.5
VMware vCenter Server 6.5.x
VMware vCenter Server 5.1.x
VMware vCenter Server 6.0.x
VMware ESXi 3.5.x Installable
VMware vSphere 7.0.x
VMware vCenter Server 6.7.x
VMware ESXi 4.1.x Embedded
VMware vSphere ESXi 6.7
VMware ESXi 4.0.x Installable
VMware vSphere ESXi 6.0
VMware vSphere ESXi 5.0
VMware vSphere ESXi 6.5
VMware ESXi 4.1.x Installable
VMware vCenter Server 5.5.x
VMware vSphere ESXi 8.0.x
VMware vSphere ESXi 5.1
VMware ESXi 4.0.x Embedded
VMware vSphere ESXi 5.5
VMware vCenter Server 6.5.x
VMware vCenter Server 5.1.x
VMware vCenter Server 6.0.x
VMware ESXi 3.5.x Installable
VMware vSphere 7.0.x
VMware vCenter Server 6.7.x
VMware ESXi 4.1.x Embedded
VMware vSphere ESXi 6.7
Cause
Bridged Protocol Data Units (BPDUs) are the frames that are exchanged between physical switches as part of the Spanning Tree Protocol (STP). STP is used to prevent loops in the network and is commonly enabled on physical switches. When a link on a physical switch port goes up, the STP protocol starts its calculation and BPDU exchange to determine if the port should be in forwarding or blocking state. Bridge Protocol Data Unit (BPDU) frames exchange across the physical switch ports to identify the Root Bridge and form a tree topology. VMware’s vSwitches do not support STP and do not participate in BPDU exchanges. If a BPDU frame is received on a vSwitch uplink, that frame is not processed for STP and traverses the vSwitch. For best practice, either the physical switch should have BPDU filters enabled or the Net.BlockGuestBPDU option on the host should be enabled in order for those BPDU frames to be blocked. The BPDU filter needs to be enabled on the physical switch or host to prevent physical ports to go down. Likewise, VMware vSwitches do not generate BPDU frames.
Note: Typically VMware vSwitches (Standard and Distributed) don't form loops by default as there is no way to join two virtual switches together at layer 2 of the OSI layer. As such, no Spanning Tree Protocol functionality has been incorporated into the virtual switches. Loops can be configured in certain situations with vSwitch features like port mirroring or bridging technologies.
The STP process of identifying root bridge and finding if the switch ports are in forwarding or blocking state takes somewhere around 30 to 50 seconds. During that time no data can be passed from those switch ports. If a server connected to the port cannot communicate for that long, the applications running on them will time out. To avoid this issue of time out on the servers, the best practice is to enable Port Fast configuration on the switch ports where the server’s NICs are connected. The Port Fast configuration puts the physical switch port immediately into STP forwarding state. For more information, see STP may cause temporary loss of network connectivity when a failover or failback event occurs (1003804).
Another recommended configuration on these vSphere host-facing switch ports is to enable BPDU guard. This configuration defines the STP boundary and keeps the topology predictable by preventing the devices connected to those ports influencing the STP topology.
The diagram below shows the spanning tree protocol boundary created due to the BPDU guard configuration on the physical switch ports. With this setup, any BPDU frame received on the physical switch port causes that port to become blocked.
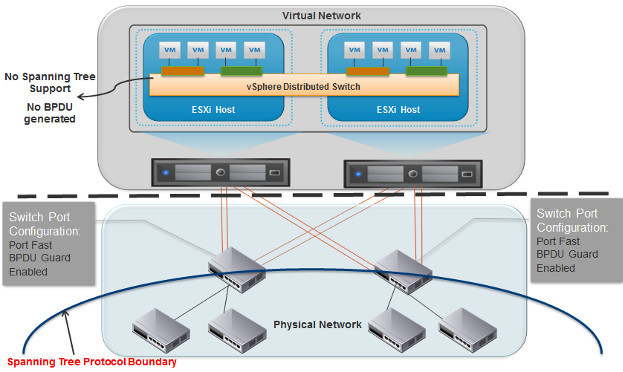
Port Fast and BPDU Guard configuration on physical switch ports
Some customers have experienced Denial of Service attack situations when a compromised virtual machine starts generating BPDU frames. In this scenario, the BPDU frames are forwarded through the vSwitch and reach physical switch ports. The physical switch in turn disables the port because of the BPDU guard configuration. To recover from this uplink traffic path failure, the vSphere host moves that virtual machine traffic to another uplink and thus disables another switch port. This ultimately creates a cluster-wide failure scenario as shown in the figure below (the red virtual machine is sending BPDU frames):
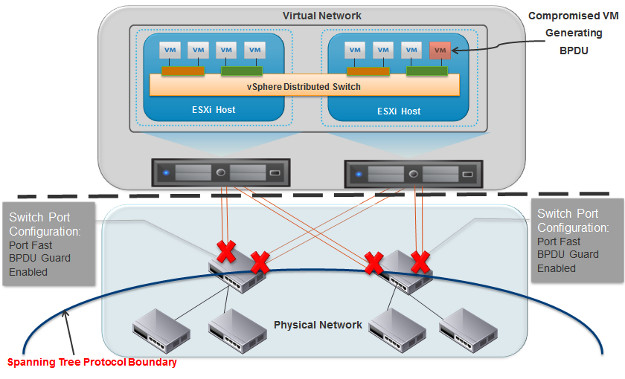
Denial of Service attack scenario
To prevent such Denial of Service attack scenarios, the BPDU filter feature is supported as part of the vSphere 5.1 and later release. After configuring this feature at the ESXi host level, BPDU frames from any virtual machine will be dropped by the vSwitch. This feature is available on both Standard and Distributed vSwitches. The diagram below shows a virtual machine (red) generating BPDUs and those BPDUs dropped by the vSwitch:
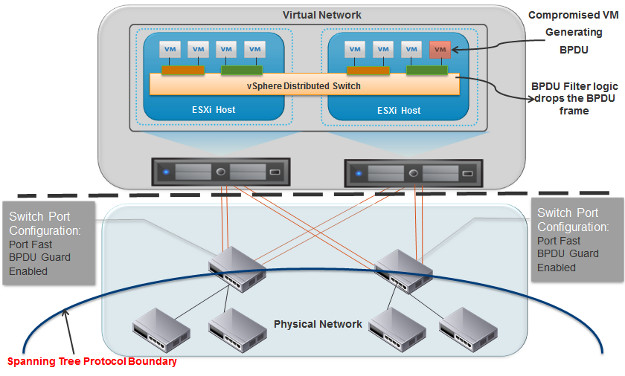
Note: Typically VMware vSwitches (Standard and Distributed) don't form loops by default as there is no way to join two virtual switches together at layer 2 of the OSI layer. As such, no Spanning Tree Protocol functionality has been incorporated into the virtual switches. Loops can be configured in certain situations with vSwitch features like port mirroring or bridging technologies.
The STP process of identifying root bridge and finding if the switch ports are in forwarding or blocking state takes somewhere around 30 to 50 seconds. During that time no data can be passed from those switch ports. If a server connected to the port cannot communicate for that long, the applications running on them will time out. To avoid this issue of time out on the servers, the best practice is to enable Port Fast configuration on the switch ports where the server’s NICs are connected. The Port Fast configuration puts the physical switch port immediately into STP forwarding state. For more information, see STP may cause temporary loss of network connectivity when a failover or failback event occurs (1003804).
Another recommended configuration on these vSphere host-facing switch ports is to enable BPDU guard. This configuration defines the STP boundary and keeps the topology predictable by preventing the devices connected to those ports influencing the STP topology.
The diagram below shows the spanning tree protocol boundary created due to the BPDU guard configuration on the physical switch ports. With this setup, any BPDU frame received on the physical switch port causes that port to become blocked.
Port Fast and BPDU Guard configuration on physical switch ports
Some customers have experienced Denial of Service attack situations when a compromised virtual machine starts generating BPDU frames. In this scenario, the BPDU frames are forwarded through the vSwitch and reach physical switch ports. The physical switch in turn disables the port because of the BPDU guard configuration. To recover from this uplink traffic path failure, the vSphere host moves that virtual machine traffic to another uplink and thus disables another switch port. This ultimately creates a cluster-wide failure scenario as shown in the figure below (the red virtual machine is sending BPDU frames):
Denial of Service attack scenario
To prevent such Denial of Service attack scenarios, the BPDU filter feature is supported as part of the vSphere 5.1 and later release. After configuring this feature at the ESXi host level, BPDU frames from any virtual machine will be dropped by the vSwitch. This feature is available on both Standard and Distributed vSwitches. The diagram below shows a virtual machine (red) generating BPDUs and those BPDUs dropped by the vSwitch:
Resolution
To enable the BPDU filter, a per-host advanced setting called
Notes:
Net.BlockGuestBPDU must be changed from a value of 0 (disabled) to 1 (enabled). This setting can be changed from the vSphere Web Client, vSphere Client, and from the command line.Notes:
- The BPDU filter setting applies only to the host it is being set on. If you wish to enable this on all hosts in the environment, the setting must be changed on all hosts individually.
- When BPDU filtering is enabled, it applies to all outbound traffic on the configured host. As such, all Standard and Distributed switch ports associated with this host will be filtered.
- By default, the BPDU filter is enabled in ESXi versions starting with 8.0. In previous versions, it was disabled by default.
- This configuration change takes effect immediately and does not require a host reboot but the setting will take effect on virtual machines if they powered on after the value has been changed. Virtual machines must be powered off and on to apply this filter.
- Using the vSphere Client, switch to the Hosts and Clusters view.
- Click the desired host from the inventory tree view in the left pane.
- Click the Configuration Tab and then Advanced Settings under Software.
- Click Net and then locate the
Net.BlockGuestBPDUoption. - Change the value to 1, which enables BPDU filtering.
- Click OK.
- Click the desired host in the inventory.
- Click the Manage Tab and then click Settings.
- Click Advanced System Settings.
- In the Filter field at the top right of the page, type BPDU to filter the results.
- A setting called
Net.BlockGuestBPDUappears. - Change the value to 1 to enable the BPDU filter.
Additional Information
For other specific use cases and recommended settings, see Denial of service due to BPDU Guard configuration (2017193).
STP may cause temporary loss of network connectivity when a failover or failback event occurs (1003804)
Configuring advanced options for ESXi/ESX
Using ESXi Shell in ESXi 5.x and 6.x
Troubleshooting Denial of Service attack in virtual infrastructure cluster
vSphere 5.1 での BPDU フィルタ機能について
了解 vSphere 5.1 中的 BPDU 筛选器功能
STP may cause temporary loss of network connectivity when a failover or failback event occurs (1003804)
Configuring advanced options for ESXi/ESX
Using ESXi Shell in ESXi 5.x and 6.x
Troubleshooting Denial of Service attack in virtual infrastructure cluster
vSphere 5.1 での BPDU フィルタ機能について
了解 vSphere 5.1 中的 BPDU 筛选器功能
Feedback
Yes
No
